If you – or the company you work for – uses FortiGate for client VPN connectivity, there’s a strong chance the setup will stop working after upgrading to FortiOS 7.6.3. Fortinet quietly deprecated and removed the SSL VPN feature (see the release notes). SSL VPN has become the de‑facto standard for client‑side VPNs across vendors, and nearly every major manufacturer – including Fortinet – has relied on it until now.
Fortinet had already announced that SSL VPN would be dropped on FortiGate models with less than 4 GB of RAM, but the blanket removal for all models was unexpected. The company hasn’t explained the rationale, though it’s likely tied to the growing number of vulnerabilities in the SSL VPN stack. Over the past few years, FortiOS has seen several critical issues in this component. Other vendors struggle with similar flaws, because SSL VPN’s architecture is far more complex than, say, IPsec.
For FortiOS, the accumulation of high‑profile vulnerabilities has hurt the product’s reputation – probably a major factor behind this decision. Either way, it has far‑reaching consequences. Even though Fortinet provides an SSL‑VPN‑to‑IPsec migration guide, switching means at least:
- modifying the firewall configuration and all affected rules
- rolling out new client versions or at least new configurations
- extensive testing, plus help‑desk and (possibly) user training
The good news: the latest FortiClient releases together with current FortiOS versions now offer an almost identical feature set when using IPsec VPN. Key new IPsec capabilities include:
- SAML‑based SSO (e.g., with Entra ID), enabling compliance checks before VPN login
- TCP transport instead of UDP
- Customizable transport port (so you can still use port 443, for instance)
Best‑practice tips for migrating to IPsec
- Deploy the new FortiClient configuration manually or via an endpoint‑management tool such as Intune—there’s no zero‑touch process yet.
- Choose TCP over UDP from day one when possible, and set the tunnel to a widely‑accepted port (e.g., 443). That maximizes compatibility with networks like public hotspots.
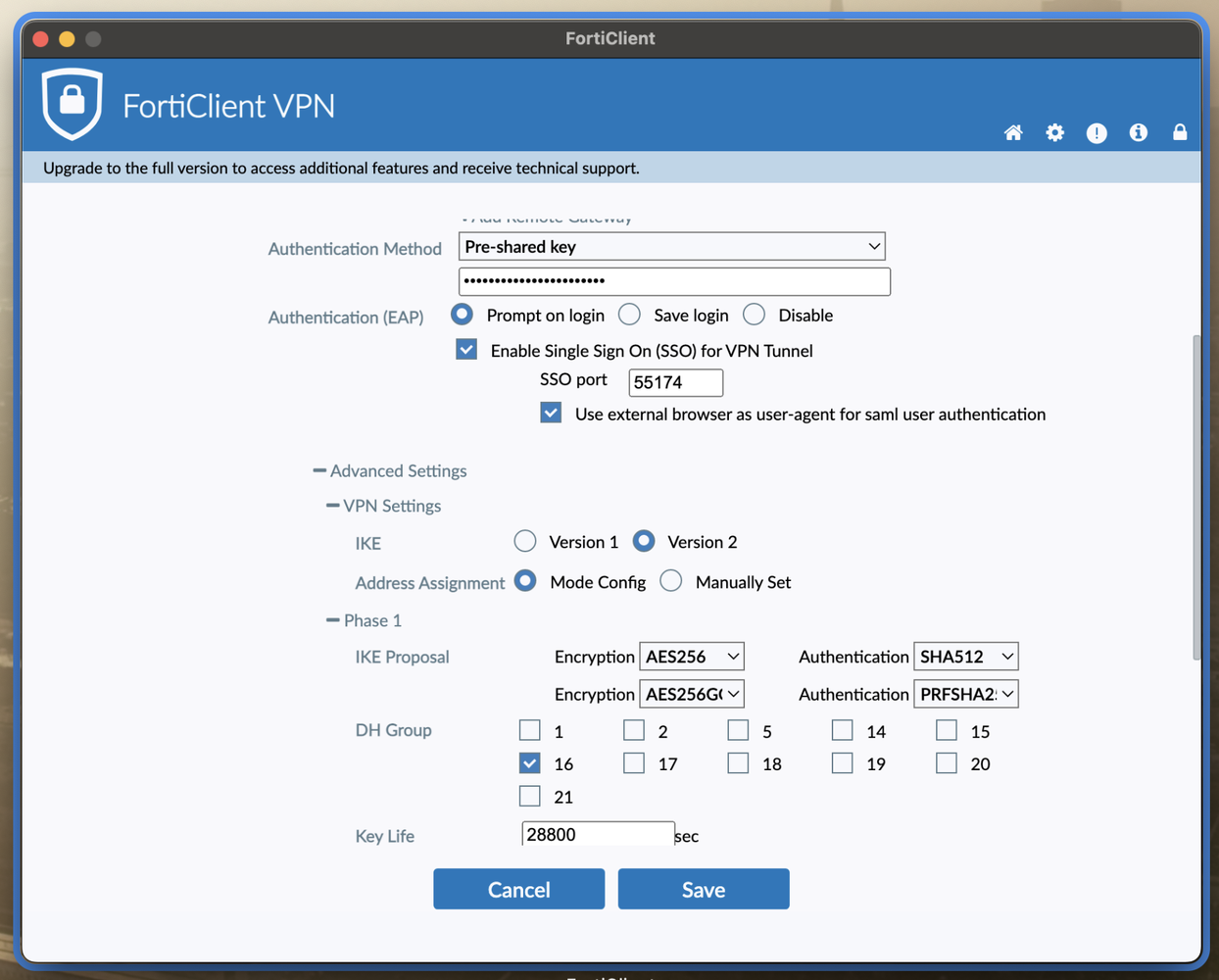
- Mind your DH groups and proposals. Different OS versions support different combinations. So far I’ve had the highest cross‑platform success (Windows, macOS, iOS—Linux and Android untested) with DH-Group 16 and AES‑256‑SHA‑512 for both Phase 1 and Phase 2.
- PSK vs. Certificate Based authentication: even when you are using a SAML authentication provider, you have to use either a pre-shared key or certificate during authentication. While PSK might be easier to maintain, using a device-bound certificate, deployed with a device management solution, might add some extra security.
At least there’s one silver lining to the feature’s removal: IPsec VPN is noticeably faster than SSL VPN.
 Tobi arbeitet seit ca. 15 Jahren schwerpunktmäßig mit Microsoft-Produkten. Nachdem er sein Cloud Hosting-Unternehmen in 2015 erfolgreich veräußerte, unterstützt er heute mittelständische und große Unternehmen bei Cloud Security und Automatisierungs-Fragen.
Tobi arbeitet seit ca. 15 Jahren schwerpunktmäßig mit Microsoft-Produkten. Nachdem er sein Cloud Hosting-Unternehmen in 2015 erfolgreich veräußerte, unterstützt er heute mittelständische und große Unternehmen bei Cloud Security und Automatisierungs-Fragen.
Keine Kommentare
Kommentar hinterlassen Abbrechen